FIPS 140-2 Level 3
Our secure elements meet Federal Information Processing Standards for cryptographic modules, ensuring they meet stringent government and financial industry requirements.
Multi-layered protection for your digital assets
At Dylimu, we implement a defense-in-depth strategy that combines hardware security, cryptographic protocols, and user-centered design to create an impenetrable barrier between your private keys and potential threats.
Our security architecture is built on the principle that no single security measure is sufficient. Instead, we layer multiple independent security mechanisms to ensure that even if one layer is compromised, your assets remain protected.
Each device undergoes rigorous security testing, including penetration testing, side-channel analysis, and fault injection attempts, to validate our security claims before reaching your hands.
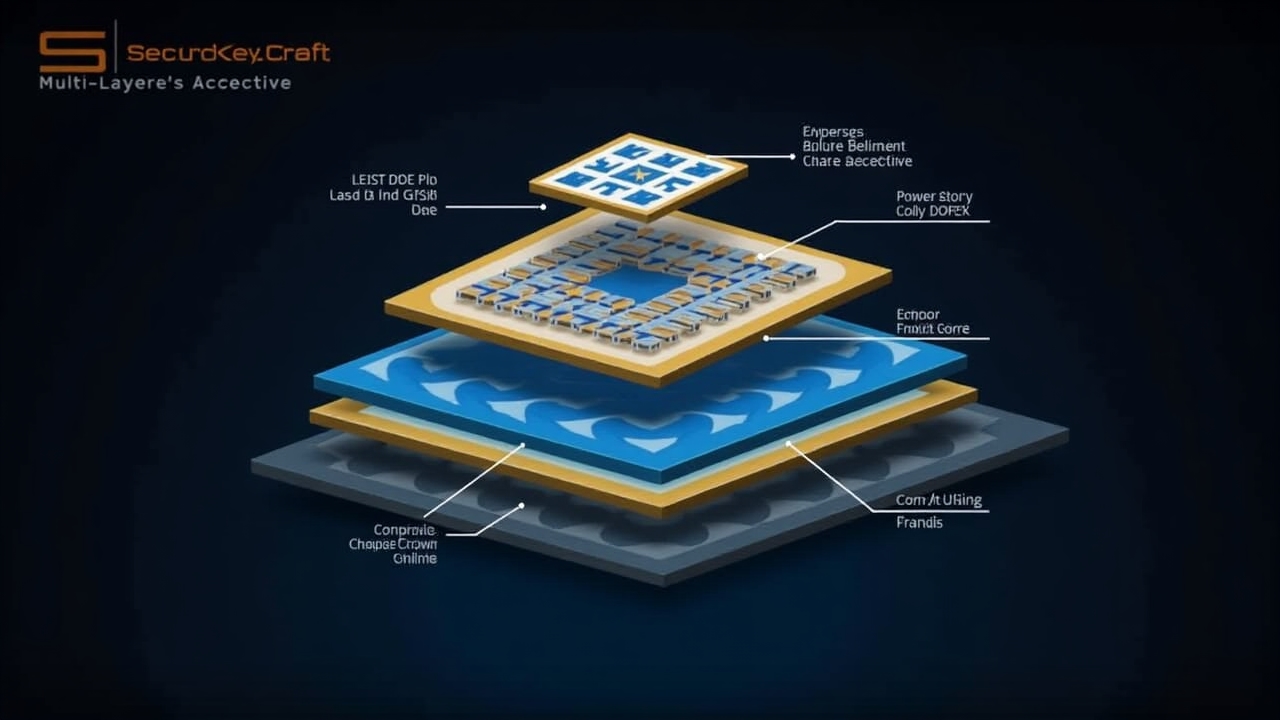
Multiple independent security layers working in concert
Our devices use specialized security chips designed to resist physical attacks and protect cryptographic secrets, even if an attacker gains physical access to the device.
We implement industry-standard cryptographic algorithms that have withstood extensive cryptanalysis, ensuring your keys remain mathematically secure against computational attacks.
Our user-centered security features provide intuitive protection against social engineering and user error, which are common vectors for cryptocurrency theft.
The cornerstone of our hardware security is the secure element chip—the same technology used in high-security applications like payment cards, passports, and military systems.
These specialized microcontrollers are designed from the ground up with security as their primary function. They include:
Our lazric security architecture ensures that even if an attacker gains physical access to your device, extracting your private keys remains practically impossible.
Complete isolation from networked threats
An air-gap is a security measure that physically isolates a computer or network from unsecured networks, such as the public Internet or an unsecured local area network.
Our hardware wallets maintain a strict air-gap, never connecting directly to the internet. This approach eliminates entire categories of remote attacks that plague software wallets and internet-connected devices.
When you need to make a transaction, the unsigned transaction data is transferred to your Dylimu device via QR code or offline USB connection. The device signs the transaction in its secure environment, and the signed transaction is then returned to your online device for broadcasting to the network.
This approach ensures that even if your computer or smartphone is compromised by malware, your cryptocurrency private keys remain secure within the isolated environment of your hardware wallet.
We believe that true security requires transparency. That's why our firmware is open source and available for public review. This approach offers several critical security benefits:
Our commitment to open source security extends to our development process, with public issue tracking, transparent security discussions, and community contributions.
function deriveKey(seed, path) {
if (!isValidSeed(seed) || !isValidPath(path)) {
throw new Error('Invalid input parameters');
}
const masterKey = secureElement.deriveMasterKey(seed);
let derivedKey = masterKey;
const segments = path.split('/');
for (const segment of segments) {
if (!segment) continue;
const hardened = segment.endsWith("'");
const index = parseInt(hardened ?
segment.slice(0, -1) : segment);
derivedKey = secureElement.deriveChildKey(
derivedKey,
index,
hardened
);
}
return secureElement.getPublicKey(derivedKey);
}
Third-party verification of our security claims
Our secure elements meet Federal Information Processing Standards for cryptographic modules, ensuring they meet stringent government and financial industry requirements.
Our devices have been evaluated against international Common Criteria standards, verifying their security functionality and assurance requirements.
Regular security audits by leading security research firms ensure our devices maintain the highest security standards against evolving threats.
Our commitment to security is ongoing. We regularly submit our devices and firmware for independent testing and maintain a security bounty program to encourage responsible disclosure of potential vulnerabilities.
What security researchers say about our approach
"The multi-layered security approach implemented by Dylimu represents the current best practices in hardware security. Their commitment to open-source development and independent security auditing demonstrates a serious approach to cryptocurrency protection."
Cryptography Researcher, MIT
"I've personally reviewed the security architecture of Dylimu devices and found their implementation of secure elements and air-gap protection to be particularly robust. Their approach to physical security deserves special mention for addressing often-overlooked attack vectors."
Hardware Security Specialist, CyberDefense Institute
Experience the peace of mind that comes with knowing your cryptocurrency private keys are protected by industry-leading security technology.
Explore Our Devices